Friday, 24th July: routine Twitter search of “iformat”.
This is generally a quick check to see what people are saying who’s sharing our stuff. Nothing ground breaking; happens all the time.
But then something weird happened.
Update: find out what happened in our short follow-up blog post!
A quick overview of Twitter search
If you’re an avid Twitter user, you might remember how earlier this year (around April) they gave their search a makeover.
Now you could sort through various tabs which sorted Tweets based on account, popularity, photos, videos, and more. It was no longer just a running stream of posts (although you could still select the tab ‘live’ for those results).
In the example below, you can see that the top result for the search “facebook” came from Hillary Clinton’s account. Not surprising, as she has 3.9 million followers, and that Tweet had been “favourited” more than 800 times.
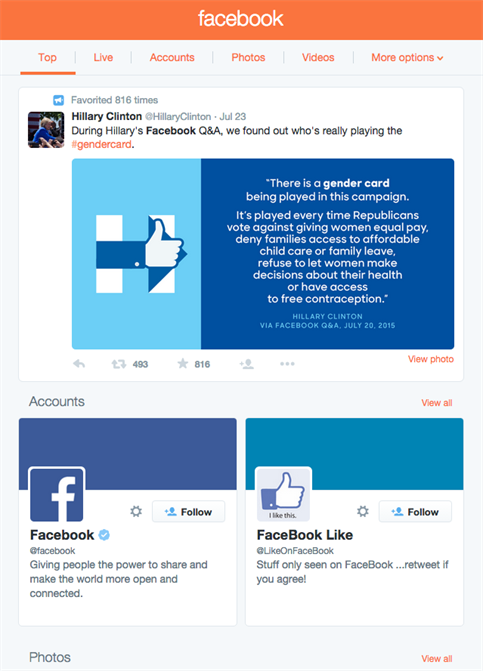
Below that, you can see Accounts, and further down, you see the heading “Photos”. All of these results are associated with the original search query.
So far, all very normal.
When you find a Twitter account impersonating your business
So when I searched “iformat” on the morning of the 24th of July, I was shocked to see not one but two accounts with our name. Now, of course, people do have the same names. There are many Matt Le Blancs and Kate Winsletts and as a result, names are bound to overlap on Twitter. Even businesses have to deal with name duplications.
But this was weird. The two accounts looked exactly the same. Same logo, same cover image, same name, and even the same description! (We had changed ours slightly just days earlier).

Then I checked the small grey Twitter handles. I saw @iformat. That was ours. But the other was the same! Maybe there was a slight glitch and they were accidentally showing two of the same account.
I squinted and realised it: the other handle was @iformct. A sneaky ‘c’ instead of an ‘a’! In that grey font, you can scarcely tell the difference!
I clicked to their profile and saw an exact replica of our page. It was weird.

- They had Tweeted 42 times
- They were following 131 accounts
- They had 15 followers
- They had “favourited” 50 Tweets
They followed a man from Norway. One from India too. Another from Washington DC. They followed a guy called Ron Kardashian. Maybe they thought he was part of the Kardashian crew. They followed a famous poodle with pink ears who referred to herself as the Princess of Beverly Hills.
I was checking every last bit of information, feeling like I was on CSI: Cyber.
All 42 of their Tweets were Retweets. There was no original content; nothing hinting to who this mystery account was, where they were from, or what they did.
Many of their Retweets were in Spanish. And their latest Retweet was on the 21st! That was only four days ago!
What to do when you think your business has been violated on Twitter
I immediately hit the gear button (next to the Follow button) with the intention of reporting the account. The pop-up required that I choose a reason for the report. The reasons were:
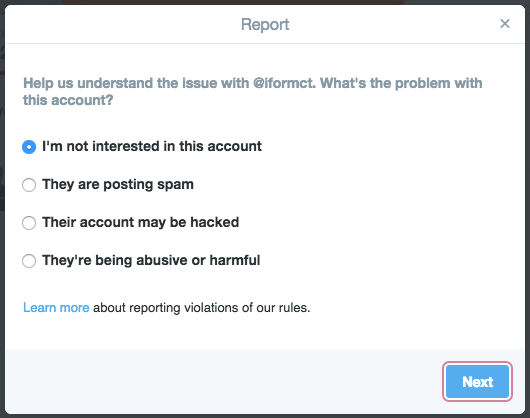
I’m not interested in this account
If I wasn’t interested, I’d just leave. If they posted boring stuff I would simply not follow them. I could block them if I really wanted to. No problem. “Disinterest” is hardly grounds for reporting.
Not the right option. Next!
They are posting spam
Not really. In fact, they were retweeting news videos and articles (plus a random cat vine and a story from Latina Magazine about JLo’s new music video). Were the from Latin America?
Like I said, a lot of their retweets were in Spanish, so I couldn’t tell if they were spam. It didn’t really look like it, though.
Moving on…
Their account may be hacked
There was no sign of hacking, and it didn’t look like they were posting anything prohibited or illicit.
I couldn’t tell if they were sending unsolicited private messages, if their password had been changed, or if it was a hacker who had made these profile and cover image changes.
Finally…
They’re being abusive or harmful
Again, nothing here indicating they were doing anything to harm others. There were no signs of threats, abusive behaviour, or harassment.
So none of those options really helped. What did help, however, was that link click advising me to “learn more about reporting violations of all our rules”.
It brought me to a page called “How to report violations”. Ah, this was better. More specificity!
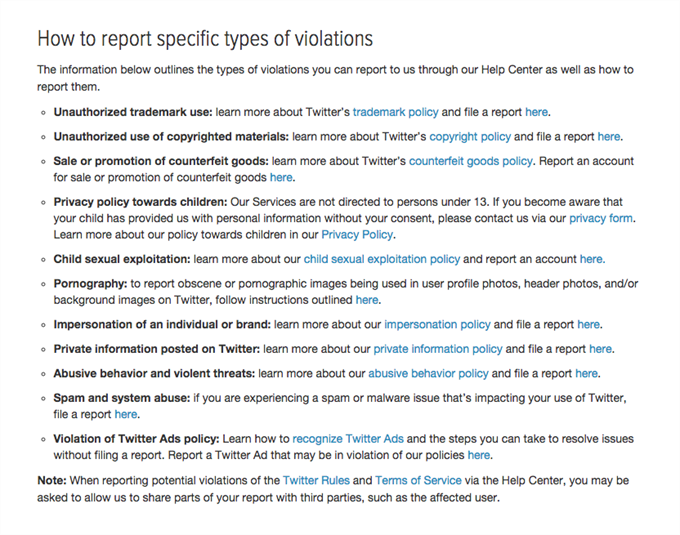
I could cancel out the majority immediately. I was left with the following:
- Unauthorised trademark use
- Unauthorised use of copyrighted materials
- Impersonation of an individual or brand
Each specific type of violation pointed to both a policy page about that particular violation, as well as a page where we could file a report.
Reporting a Twitter account for impersonation of an individual or brand
We chose to begin with the third report, impersonation of an individual or brand. We figured we would start here, and if needed, we could escalate the issue to one of the other options.
We hoped this attempt would be enough, though.
The report was pretty straightforward to fill out. It took just a few minutes to carefully complete, and so we submitted the form.
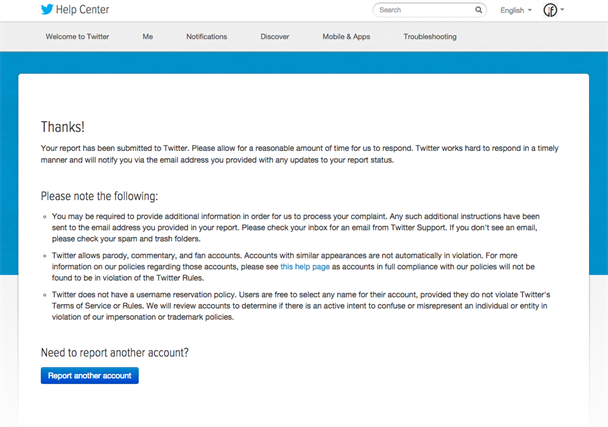
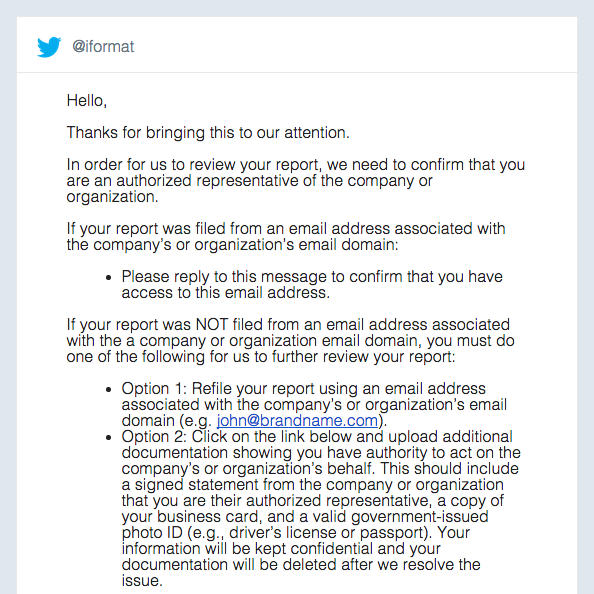
For what it’s worth, submit your report through an email associated with your company to avoid this extra step!
When they say “additional documentation”, they mean it: “a signed statement from the company or organization that you are their authorized representative, a copy of your business card, and a valid government-issued photo ID (e.g., driver’s license or passport).” What a drainer!
I responded to this email confirming that I had access to this email address, and then… I waited.
Update: find out what happened in our short, follow-up blog post!